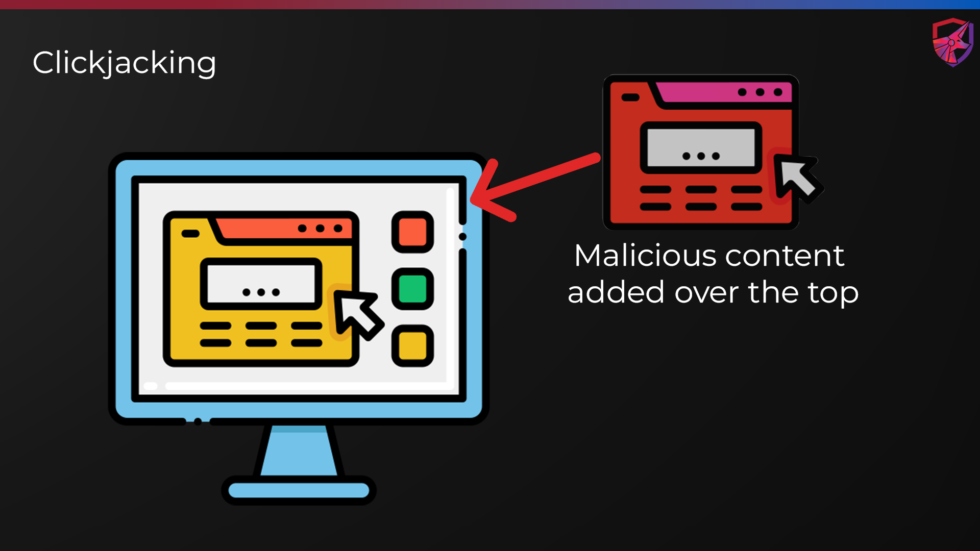
Advanced Clickjacking Python
Automated clickjacking vulnerability scanner for web applications. Detects and reports potential security flaws with detailed exploitation methods.

Automated clickjacking vulnerability scanner for web applications. Detects and reports potential security flaws with detailed exploitation methods.

Cross-Site Request Forgery (CSRF) is an attack that tricks an authenticated user's browser into executing unintended, malicious actions on a trusted website.

Module helps identify and analyze CRLF injection vulnerabilities in web applications, enhancing security by preventing header injection attacks.
Identifies vulnerabilities related to the Host header in HTTP requests, helping to prevent potential security risks.
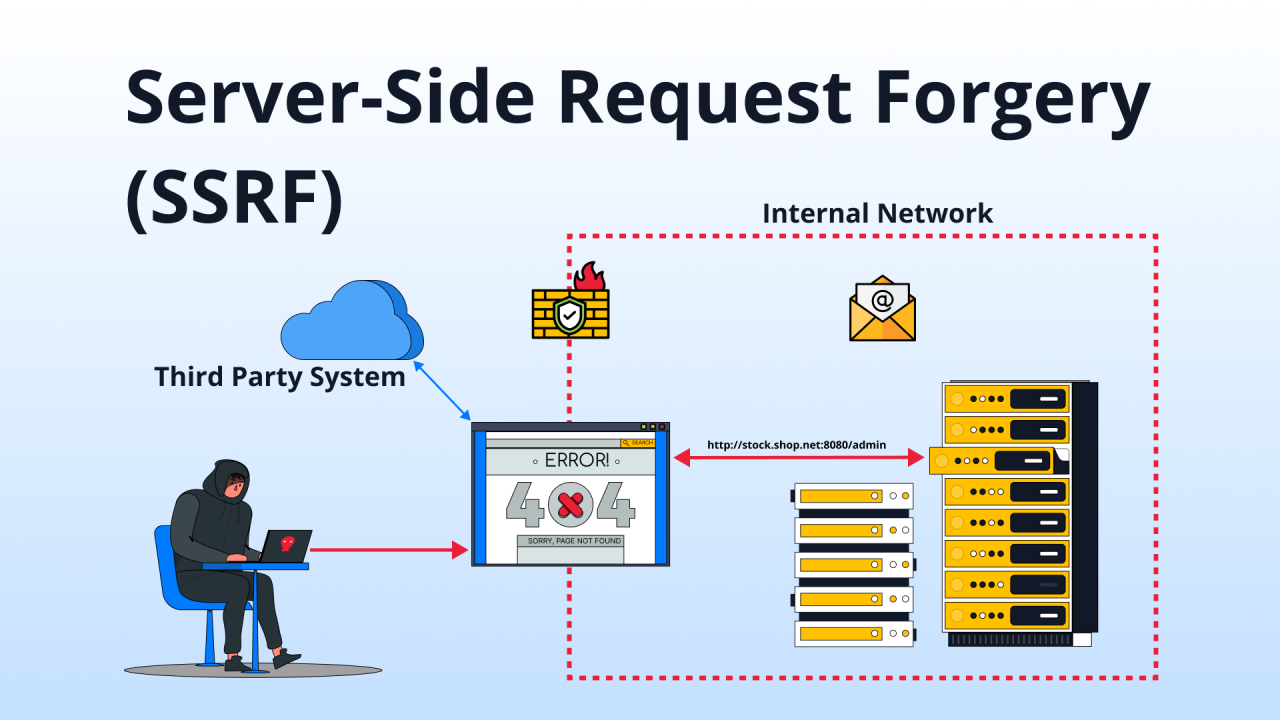
Helps identify and analyze Server-Side Request Forgery vulnerabilities, enhancing security by detecting potential SSRF attack vectors.
Helps identify Insecure Direct Object Reference vulnerabilities by enumerating object IDs.
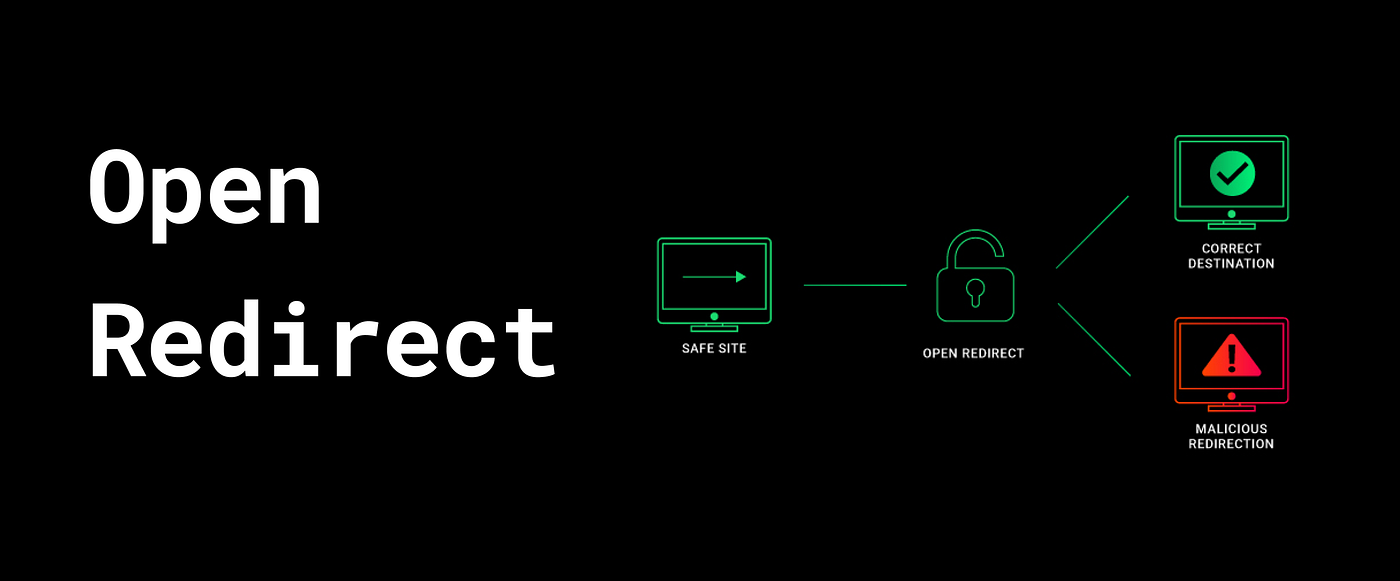
Helps identify open redirect vulnerabilities by testing URL redirection parameters.

Tests file upload functionality for security vulnerabilities.

Detects HTTP Parameter Pollution vulnerabilities in web applications.
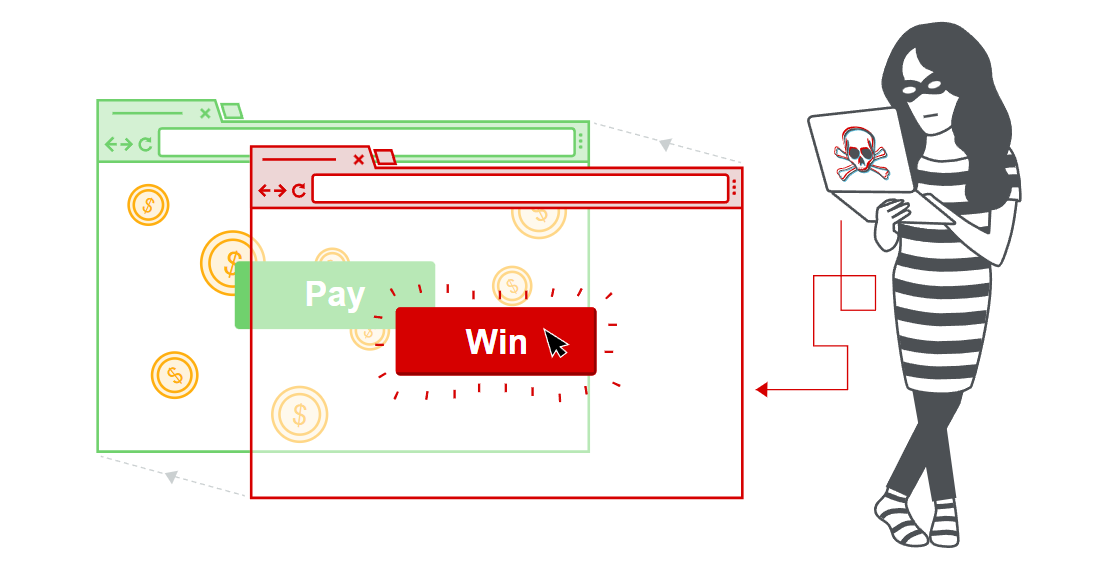
A simple HTML template for demonstrating clickjacking attacks. Use this for educational purposes to understand the risks and mitigation strategies.

A simple Python script for demonstrating clickjacking attacks to find vulnerabilities via python script.

CSP vulnerability scanner to identify configuration gaps and potential security risks in Content Security Policy implementations.
Rate limiting stress testing tool to evaluate the robustness and effectiveness of rate limiting mechanisms under high load conditions.

Analyzes HTTP requests to detect smuggling vulnerabilities that can bypass security controls and poison caches.

Analyzes web cache poisoning vulnerabilities to identify potential attack surfaces and improve cache security.
Analyzes GraphQL APIs to identify introspection capabilities and potential exploitation vectors.
